Stockholder Privacy and Security
Protect yourself and your business
Arming yourself with knowledge on how cyber criminals are operating — and the tricks they have up their sleeves — is the best defense against cyber-attacks for your household or business.
What are three simple measures you can take to ensure your information is shielded from these malicious cyber attackers?

Identify and avoid scam emails, texts, and calls that steal your money
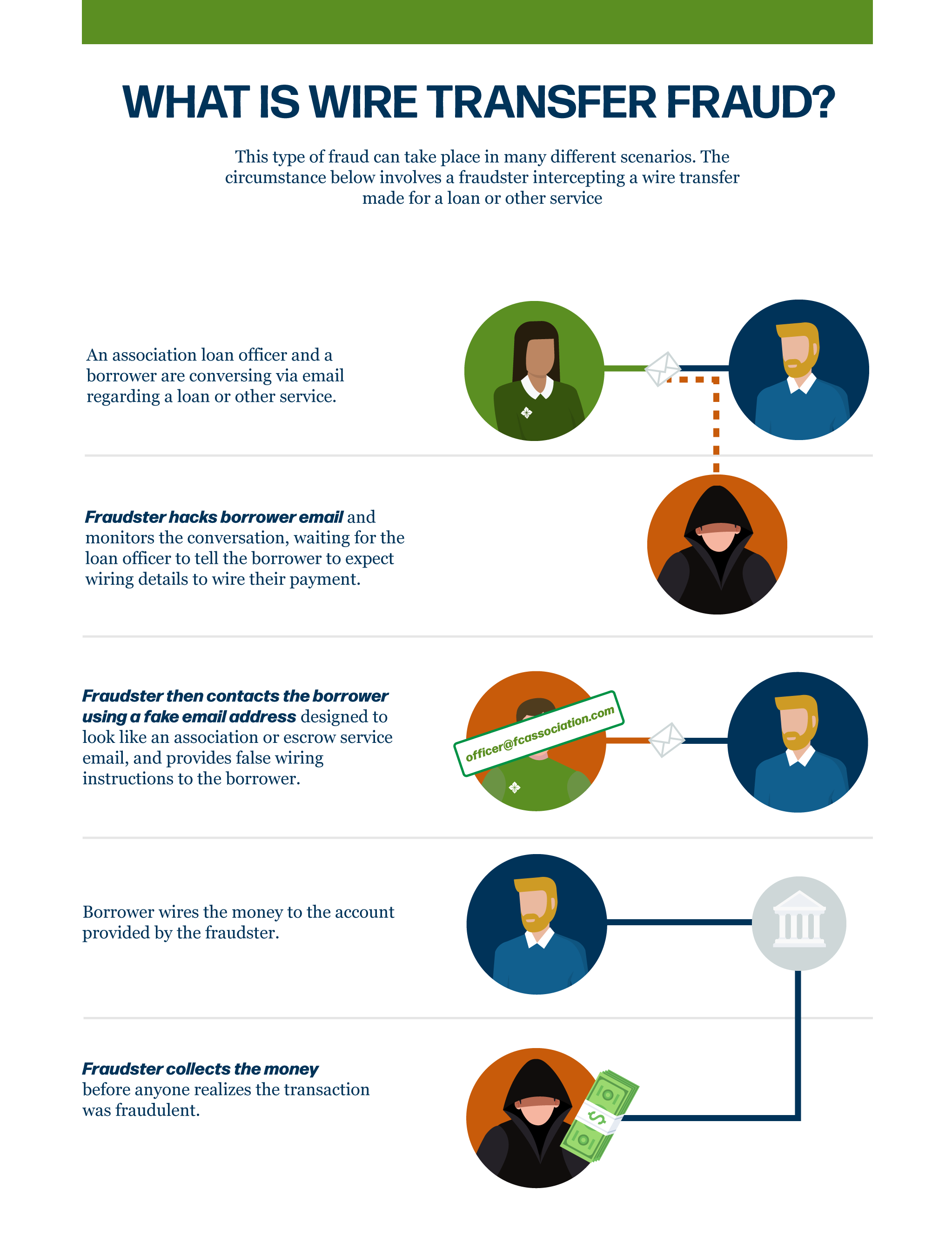
Attackers may hack into potential borrower email accounts, wait for the right time, then try to trick victims and redirect legitimate payments to themselves.
These attempts appear to come from a credible source and are timed to perfection … because they've been watching. Hackers may pounce right when a loan is closing and attempt to provide a last-minute change to wiring instructions. Blindly following the instructions, and ignoring the red flags, could result in borrowers wiring money to the attackers. These instantaneous transfers of money are almost impossible to recover if sent to the wrong source.
Watch for these red flags in email, SMS, and voicemail:
- ⚑Urgency: act NOW
- ⚑Authority: it looks official
- ⚑Emotion: inspires panic, fear, hope, or curiosity
If you've received a suspicious email:
- Call the institution directly using the phone number on their website
- Send a new email using the address you have on file - do not respond to any email that appears suspicious
In the meantime, protect your email account by enabling Multifactor Authentication (MFA) to prevent a hacker gaining access.
Secure and update your devices so they cannot be taken over
Don’t give attackers an easy way in. Keeping your devices up to date secures them from the latest risks. Do the following:
Cell Phones
- Enable lock screen pin/password and biometrics (fingerprint/face ID) - and avoid reuse of passwords between devices.
- Set the device to automatically update when latest software versions are available.
- Enable cloud backups.
- Enable “find my device” if available. You can track the location of a stolen device, lock it remotely, erase data remotely, and retrieve backup data from the device.
Laptop/Desktop
- Enable passwords & biometrics if (available).
- Use drive encryption technology that can help protect your files even if the drive is stolen. BitLocker/FileVault are built into Windows and are a free service. Encrypted files are inaccessible without the correct pin.
- Ensure your antivirus software is enabled; it’s built-in and free with most modern operating systems.
- Keep your operating system up to date. Enable automatic updates from the manufacturer.
- Back up your data preferably disconnected from any network, but use a cloud provider if necessary. These can be scheduled to occur real-time.
- Enable “find my device” if available. You can track the location of a stolen device, lock it remotely, erase data remotely, and retrieve backup data from the device.
- Turn on you operating system built-in firewall. It’s built into your operating system and adds another layer of security on your system that will ensure connections to your computer are legitimate.
- Use a password manager to securely store your accounts and passwords. These services can also help with password strength along with resetting passwords for you.

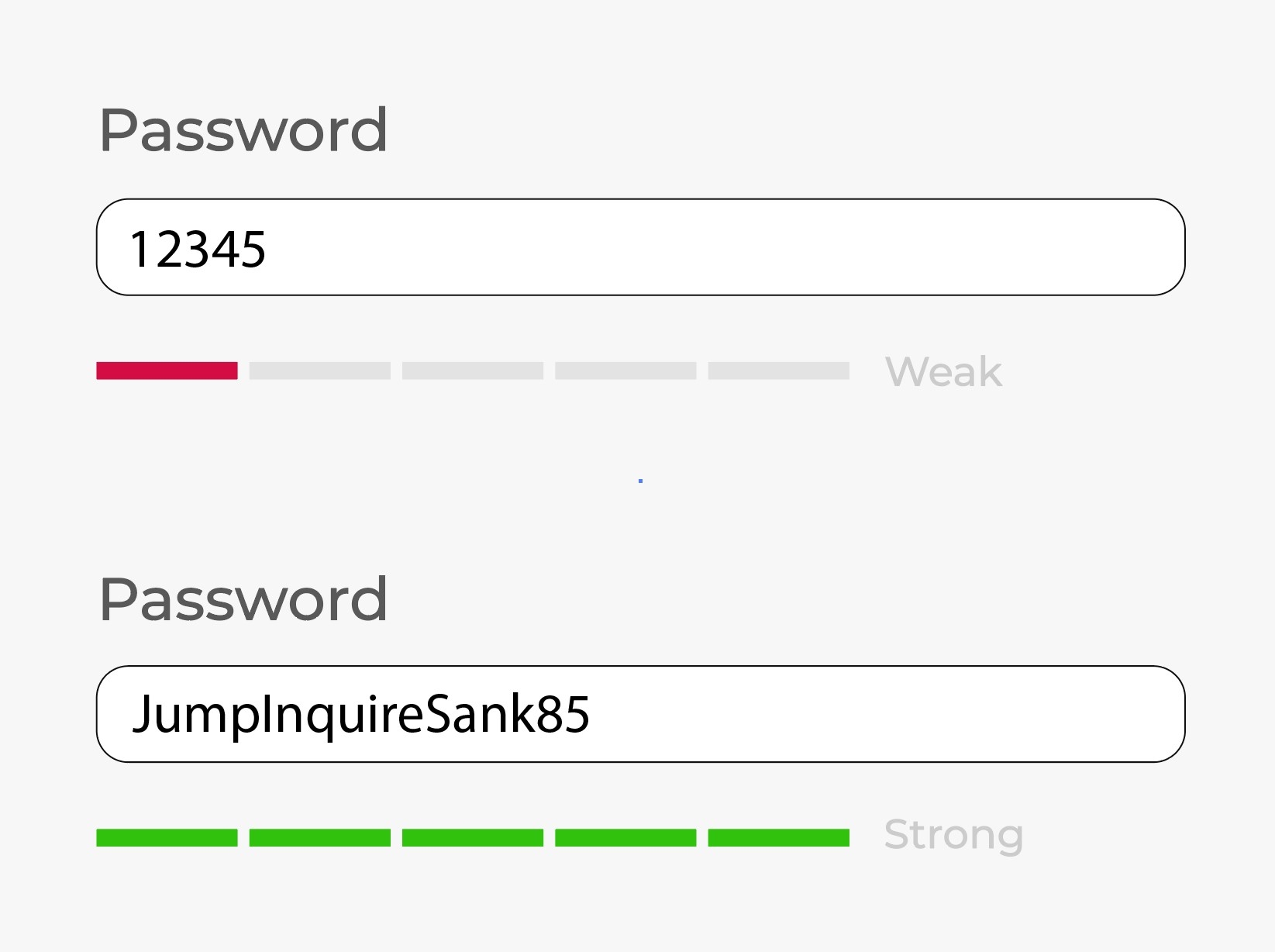
Use hard to guess passwords are stop account being hijacked
Cyber-criminals prey on people who use simple and easy-to-guess passwords, reused passwords and unchanged default passwords.
- Use a unique password for each service, device and account
- Change default passwords for each service, device and account, including your Wi-Fi network. Unchanged default administrator passwords make easy targets when attackers gain access.
- Make your password strong and unique to every device and service. It needs to be both complex and long to avoid easy guesses by malicious actors that use dictionaries or listings of leaked passwords available on the dark web.
- Don’t use personal identifiers.
- Enable two-factor/multi-factor authentication. Even if your password is guessed, having a code sent to your phone by text or an authenticator app means a malicious actor still can’t access your device or account.
- Use a password manager to securely store your accounts and passwords. These services can also help with password strength along with resetting passwords for you.
Telephone Spoofing
Ransomware attacks
Here are some tips to protect against ransomware attacks.
Keeping Your Information Secure
Here are some tips to keep your information secure.